Настройка мостового сервера OpenVPN с одной общедоступной сетевой картой IP
Я пытался настроить соединенный сервер OpenVPN без особого успеха. У меня есть VPS под управлением Ubuntu с одной сетевой картой, которая назначила ему статический публичный IP-адрес. Я хочу иметь возможность подключить к нему пару клиентов и сформировать сеть, которая работала бы как обычная локальная сеть с работающим вещанием.
Схема физических соединений:
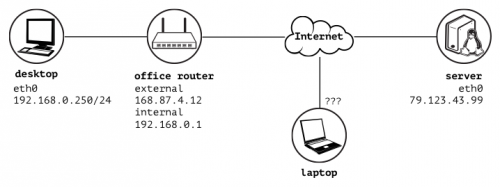
Я хотел бы иметь laptop и desktop и server в одной сети, скажем, 10.0.0.0/24. С помощью приведенной ниже конфигурации я смог подключиться только к серверу OpenVPN, но фактического соединения между машинами нет. Самое большее, что у меня получилось, это то, что server может видеть только ARP запросы, поступающие от клиентов, но не отправляет никакого ответа. Я не могу пинговать server от любого клиента, любого любого клиента из server. Я явно делаю что-то не так, но не могу понять, в чем дело. Пожалуйста, скажите мне, что где-то есть опечатка.
server' с интерфейсы:
root@server:~# cat /etc/network/interfaces
auto lo
iface lo inet loopback
auto eth0
iface eth0 inet manual
up ip link set $IFACE addr f2:3c:91:69:33:c2 promisc on up
down ip link set $IFACE down
auto tap0
iface tap0 inet manual
pre-up openvpn --mktun --dev $IFACE
up ip link set $IFACE addr f2:3c:91:69:33:c1 promisc on up
down ip link set $IFACE down
post-down openvpn --rmtun --dev $IFACE
auto br0
iface br0 inet dhcp
bridge_ports eth0 tap0
bridge_fd 0
bridge_stp off
pre-up ip link set $IFACE addr f2:3c:91:69:33:c3 # DHCP filters by MAC
server Включена переадресация IPv4:
root@server:~# sysctl -p
net.ipv4.ip_forward = 1
server конфигурация:
proto udp
dev tap0
port 1194
local vpn.server.tld
server-bridge 10.0.0.2 255.255.255.0 10.0.0.128 10.0.0.254
push "route 10.0.0.0 255.255.255.0"
client-to-client
ca keys/ca.crt
cert keys/server.crt
key keys/server.key
dh keys/dh1024.pem
tls-server
tls-auth keys/ta.key 0
user nobody
group nogroup
persist-key
persist-tun
keepalive 10 60
comp-lzo
status /var/log/openvpn.status
log /var/log/openvpn.log
verb 3
desktop конфигурация:
client
proto udp
dev tap
port 20251 # forwarded in office router
remote vpn.server.tld 1194
ca ../keys/ca.crt
cert ../keys/tomasz@desktop.crt
key ../keys/tomasz@desktop.key
tls-client
tls-auth ../keys/ta.key 1
ns-cert-type server
persist-key
persist-tun
keepalive 10 60
comp-lzo
resolv-retry infinite
server журнал подключений:
root@server:~# tail -n 40 -f /var/log/openvpn.log
Sat Jul 27 00:32:30 2013 OpenVPN 2.2.1 x86_64-linux-gnu [SSL] [LZO2] [EPOLL] [PKCS11] [eurephia] [MH] [PF_INET6] [IPv6 payload 20110424-2 (2.2RC2)] built on Feb 13 2013
Sat Jul 27 00:32:30 2013 NOTE: when bridging your LAN adapter with the TAP adapter, note that the new bridge adapter will often take on its own IP address that is different from what the LAN adapter was previously set to
Sat Jul 27 00:32:30 2013 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts
Sat Jul 27 00:32:30 2013 Diffie-Hellman initialized with 1024 bit key
Sat Jul 27 00:32:30 2013 Control Channel Authentication: using 'keys/ta.key' as a OpenVPN static key file
Sat Jul 27 00:32:30 2013 Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Sat Jul 27 00:32:30 2013 Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
Sat Jul 27 00:32:30 2013 TLS-Auth MTU parms [ L:1574 D:166 EF:66 EB:0 ET:0 EL:0 ]
Sat Jul 27 00:32:30 2013 Socket Buffers: R=[212992->131072] S=[212992->131072]
Sat Jul 27 00:32:30 2013 TUN/TAP device tap0 opened
Sat Jul 27 00:32:30 2013 TUN/TAP TX queue length set to 100
Sat Jul 27 00:32:30 2013 Data Channel MTU parms [ L:1574 D:1450 EF:42 EB:135 ET:32 EL:0 AF:3/1 ]
Sat Jul 27 00:32:30 2013 GID set to nogroup
Sat Jul 27 00:32:30 2013 UID set to nobody
Sat Jul 27 00:32:30 2013 UDPv4 link local (bound): [AF_INET]79.123.43.99:1194
Sat Jul 27 00:32:30 2013 UDPv4 link remote: [undef]
Sat Jul 27 00:32:30 2013 MULTI: multi_init called, r=256 v=256
Sat Jul 27 00:32:30 2013 IFCONFIG POOL: base=10.0.0.128 size=127, ipv6=0
Sat Jul 27 00:32:30 2013 Initialization Sequence Completed
Sat Jul 27 00:32:44 2013 MULTI: multi_create_instance called
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 Re-using SSL/TLS context
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 LZO compression initialized
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 Control Channel MTU parms [ L:1574 D:166 EF:66 EB:0 ET:0 EL:0 ]
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 Data Channel MTU parms [ L:1574 D:1450 EF:42 EB:135 ET:32 EL:0 AF:3/1 ]
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 Local Options hash (VER=V4): '360696c5'
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 Expected Remote Options hash (VER=V4): '13a273ba'
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 TLS: Initial packet from [AF_INET]89.77.180.128:20251, sid=d27be456 62dc0bf7
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 VERIFY OK: depth=1, /C=**/ST=**/L=**/O=**/CN=**_Certification_Authority
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 VERIFY OK: depth=0, /C=**/ST=**/L=**/O=**/CN=tomasz@desktop
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 Data Channel Encrypt: Cipher 'BF-CBC' initialized with 128 bit key
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 Data Channel Decrypt: Cipher 'BF-CBC' initialized with 128 bit key
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC authentication
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024 bit RSA
Sat Jul 27 00:32:44 2013 168.87.4.12:20251 [tomasz@desktop] Peer Connection Initiated with [AF_INET]168.87.4.12:20251
Sat Jul 27 00:32:44 2013 tomasz@desktop/168.87.4.12:20251 MULTI_sva: pool returned IPv4=10.0.0.128, IPv6=1::2100:0:0:0
Sat Jul 27 00:32:46 2013 tomasz@desktop/168.87.4.12:20251 PUSH: Received control message: 'PUSH_REQUEST'
Sat Jul 27 00:32:46 2013 tomasz@desktop/168.87.4.12:20251 send_push_reply(): safe_cap=960
Sat Jul 27 00:32:46 2013 tomasz@desktop/168.87.4.12:20251 SENT CONTROL [tomasz@desktop]: 'PUSH_REPLY,route 10.0.0.0 255.255.255.0,route-gateway 10.0.0.2,ping 10,ping-restart 60,ifconfig 10.0.0.128 255.255.255.0' (status=1)
Sat Jul 27 00:32:47 2013 tomasz@desktop/168.87.4.12:20251 MULTI: Learn: aa:7c:1d:c2:42:e1 -> tomasz@desktop/168.87.4.12:20251
server' s маршруты и интерфейсы с запущенным OpenVPN:
root@remote:~# netstat -rn
Kernel IP routing table
Destination Gateway Genmask Flags MSS Window irtt Iface
default 79.123.43.1 0.0.0.0 UG 0 0 0 br0
79.123.43.0 * 255.255.255.0 U 0 0 0 br0
root@server:~# ifconfig
br0 Link encap:Ethernet HWaddr f2:3c:91:69:33:c3
inet addr:79.123.43.99 Bcast:79.123.43.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:450 errors:0 dropped:0 overruns:0 frame:0
TX packets:467 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:48685 (48.6 KB) TX bytes:53043 (53.0 KB)
eth0 Link encap:Ethernet HWaddr f2:3c:91:69:33:c2
UP BROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metric:1
RX packets:20803 errors:0 dropped:0 overruns:0 frame:0
TX packets:26066 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2190355 (2.1 MB) TX bytes:3683757 (3.6 MB)
Interrupt:76
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:1183 errors:0 dropped:0 overruns:0 frame:0
TX packets:1183 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:433649 (433.6 KB) TX bytes:433649 (433.6 KB)
tap0 Link encap:Ethernet HWaddr f2:3c:91:69:33:c1
UP BROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metric:1
RX packets:6 errors:0 dropped:0 overruns:0 frame:0
TX packets:39 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:1158 (1.1 KB) TX bytes:3390 (3.3 KB)
desktop' журнал подключений s:
tomasz@desktop:$ sudo openvpn --config desktop.ovpn
Sat Jul 27 00:58:33 2013 OpenVPN 2.3.2 x86_64-apple-darwin12.4.0 [SSL (OpenSSL)] [LZO] [eurephia] [MH] [IPv6] built on Jul 24 2013
Sat Jul 27 00:58:33 2013 Control Channel Authentication: using '../keys/ta.key' as a OpenVPN static key file
Sat Jul 27 00:58:33 2013 UDPv4 link local (bound): [undef]
Sat Jul 27 00:58:33 2013 UDPv4 link remote: [AF_INET]79.123.43.99:1194
Sat Jul 27 00:58:33 2013 [vpn.server.tld] Peer Connection Initiated with [AF_INET]79.123.43.99:1194
Sat Jul 27 00:58:36 2013 TUN/TAP device /dev/tap0 opened
Sat Jul 27 00:58:36 2013 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
Sat Jul 27 00:58:36 2013 /sbin/ifconfig tap0 delete
ifconfig: ioctl (SIOCDIFADDR): Can't assign requested address
Sat Jul 27 00:58:36 2013 NOTE: Tried to delete pre-existing tun/tap instance -- No Problem if failure
Sat Jul 27 00:58:36 2013 /sbin/ifconfig tap0 10.0.0.128 netmask 255.255.255.0 mtu 1500 up
route: writing to routing socket: File exists
add net 10.0.0.0: gateway 10.0.0.2: File exists
Sat Jul 27 00:58:36 2013 Initialization Sequence Completed
desktop' s маршруты и интерфейсы с запущенным OpenVPN:
tomasz@desktop$ ifconfig
en1: flags=8863<UP,BROADCAST,SMART,RUNNING,SIMPLEX,MULTICAST> mtu 1500
ether 00:26:bb:10:6e:14
inet6 fe80::226:bbff:fe10:6e14%en1 prefixlen 64 scopeid 0x5
inet 192.168.0.250 netmask 0xffffff00 broadcast 192.168.0.255
media: autoselect
status: active
tap0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> mtu 1500
ether aa:7c:1d:c2:42:e1
inet 10.0.0.128 netmask 0xffffff00 broadcast 10.0.0.255
open (pid 14700)
tomasz@desktop$ netstat -rn
Routing tables
Internet:
Destination Gateway Flags Refs Use Netif Expire
default 192.168.0.1 UGSc 15 760 en1
10/24 link#8 UC 2 0 tap0
10.0.0.255 ff:ff:ff:ff:ff:ff UHLWbI 0 4 tap0
127 127.0.0.1 UCS 0 0 lo0
127.0.0.1 127.0.0.1 UH 7 1873 lo0
169.254 link#5 UCS 0 0 en1
192.168.0 link#5 UCS 3 0 en1
192.168.0.1 80:c6:ab:cf:61:54 UHLWIir 16 4568 en1 704
192.168.0.250 127.0.0.1 UHS 0 0 lo0
192.168.0.255 ff:ff:ff:ff:ff:ff UHLWbI 0 4 en1
При попытке пропинговать server с desktop:
tomasz@desktop:~$ ping -c 1 10.0.0.2
PING 10.0.0.2 (10.0.0.2): 56 data bytes
--- 10.0.0.2 ping statistics ---
1 packets transmitted, 0 packets received, 100.0% packet loss
tomasz@server:~$ sudo tcpdump -nel -i tap0
tcpdump: WARNING: tap0: no IPv4 address assigned
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tap0, link-type EN10MB (Ethernet), capture size 65535 bytes
01:02:44.023108 8a:13:46:10:03:ac > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Request who-has 10.0.0.2 tell 10.0.0.128, length 28
